HITRUST with limited resources
ESP Case study: HITRUST in the age of limited resources
The Health Information Trust Alliance (HITRUST) Common Security Framework (CSF) attempted to standardize and simplify cyber security compliance for healthcare organizations by consolidating security controls from multiple standards (ex, HIPAA, PCI DSS, COBIT, NIST, and ISO, among others). However, as a matter of practical implementation, assessing and closing compliance gaps with this comprehensive standard requires a significant organizational investment in staff and resources. This can represent a barrier to HITRUST implementation for many organizations.
Our white paper, "HITRUST Security Controls: Overcoming the Cyber Security Talent Gap through Automation" discusses a number of practical problems that organizations encounter when trying to implement HITRUST and identifies ways to solve those problems through automation. Examples of capabilities provided by the Elemental Security Platform (ESP) are detailed to demonstrate the practical implementation of those strategies and solutions.
Click here to request the ESP HITRUST white paper or an online demo
Related blog post: Compliance in the age of limited resources, the case for automation
Problem 1: Lack of visibility into assets and controls impedes management processes
Manual tasks associated with gathering and analysis of information about assets and controls can add significant costs and delays to the implementation of compliance controls. Such inefficiencies can be easily eliminated through the use of automation. ESP continuously collects detailed information about each managed host within the HITRUST compliance scope, creating a comprehensive and searchable database of host attributes (characteristics) and deployed ESP rules (technical controls). By continuously gathering, analyzing, and recording this information through the use of automation tools like ESP, your team can focus on higher-level tasks needed to reach your compliance goals.
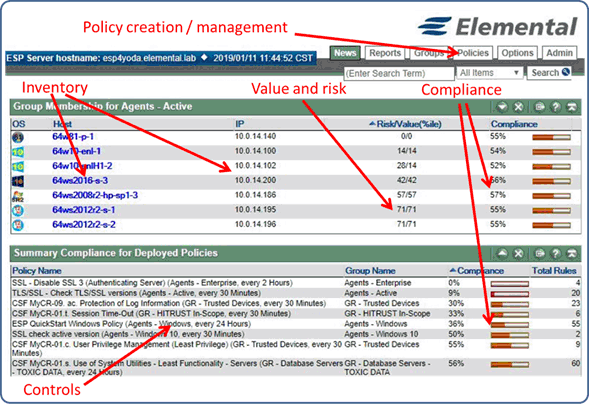
Problem 2: Overlapping compliance frameworks lead to duplication of compliance processes
ESP policy editing tool can be easily used to deploy security policies from multiple frameworks (PCI, NIST, ISO, etc) to the same group of hosts. ESP automates the underlying processes needed to document all of the deployed ESP rules, calculate compliance outcomes for each policy, and provides a set of reports detailing compliance results for each deployed policy. Utilizing one tool to manage and track controls for multiple compliance standards reduces the need for additional staff members to perform those tasks.
Problem 3: Diverse security environments lead to policy fragmentation
Some security tools only function in specific virtual- or cloud-specific environments, while others rely heavily on OS-specific tools (for example, MS Windows Group Policy Objects). Pulling together data from multiple environments is inefficient and requires a variety of specialized knowledge that many organizations lack. Environment agnostic automation solutions such as ESP provide a significant performance edge in diverse environments. Since ESP policies are platform-, location-, and environment-independent, your organization can realize a quick and uniform implementation of security policies across all environments with a click of a button. This provides significant savings in project costs.
Problem 4: Coping with the rapid changes to HITRUST controls and other related security standards
ESP can allow compliance teams to fast-forward through weeks and even months of analysis and data gathering to implement the changes. ESP offers ESP HITRUST policy templates that have been pre-arranged to match the structure of HITRUST CSF controls. As new versions of CSF become available, Elemental updates the ESP HITRUST policy templates with new sets of technical rules (controls) and makes them ready for immediate deployment, assessment, and enforcement. Implementing changes to HITRUST framework could be as easy as installing and deploying a new policy template file, so your team can move quickly to address compliance gaps.
Problem 5: Determining which assets are in scope requires extensive analysis
Control of compliance scope is one of the easiest ways to tackle compliance costs within the organization. ESP unique dynamic grouping and micro-segmentation capabilities allow your team to accurately identify all the hosts that should be considered for inclusion in the HITRUST compliance scope. Those hosts can then be grouped together and isolated from out-of-scope hosts to keep compliance scope as narrow as possible.
Problem 6: Difficulty assessing the compliance gap
Assessing the gap between the compliance controls outlined by the Governance, Risk, and Compliance (GRC) team and the actual state of security controls at the information system level has long been a struggle for compliance managers. Organizations lacking the manpower necessary to perform this process face a multitude of costly delays during their preparation for HITRUST certification. ESP was specifically designed to automate the gap assessment process to the largest extent possible. ESP gathers, analyzes, and re-calculates compliance gap scores continuously at multiple time points throughout each day, ensuring that the GRC team receives most up-to-date information obtained directly from the information systems.
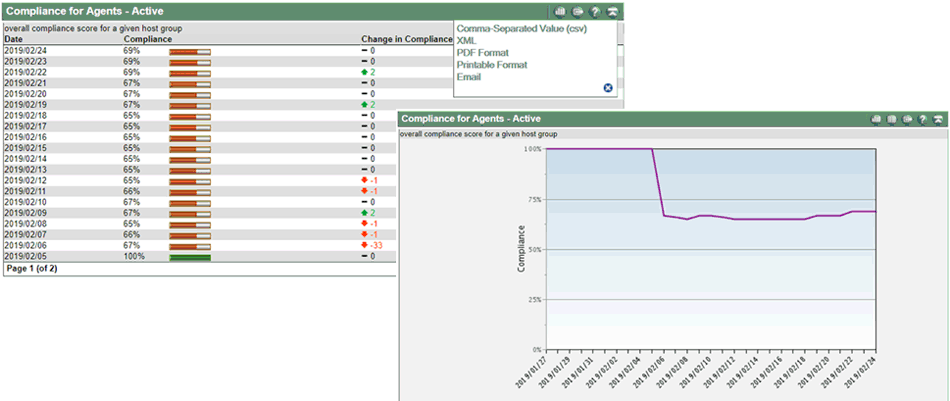
Problem 7: Difficulty closing the compliance gap
Closing known compliance gaps often involves management of complex policies, firewall rules, scripts, and other static tools. This adds to the complexity and operational overhead. We recommend focusing on minimizing the number of tools needed to close the compliance gap. In that regard, ESP is the most automated and integrated security policy enforcement solution on the market. It's unparalleled HITRUST control enforcement capabilities allow your organization to reach target compliance levels much faster than through manual and fragmented processes.
Problem 8: Lack of practical integration between risk management and compliance management
Risk-driven security compliance model remains an ideal rather than a practical model for most organizations due to lack of coordination between risk, compliance, and security teams. ESP is currently the only software platform that truly automates and integrates risk and compliance management tasks into one set of actionable security rules (controls). As a part of its automated data collection process, ESP continuously identifies, quantifies, and records various value and risk parameters for each managed host. Aggregated risk, value, and compliance information are available from a single management console. This allows risk, compliance, and security projects to run in sync with one another. As compliance gaps are closed by the security team, the risk scores of the hosts within the policy scope improve simultaneously. With ESP, even small and medium-sized organizations with limited risk experience can plan and economically execute risk-driven compliance initiatives on a continuous basis.
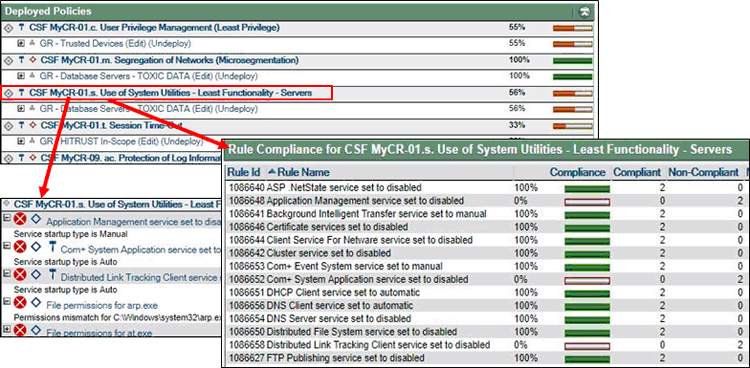
Problem 9: Manual management of security policies consumes limited staff resources
Most security policies on networks are managed with static tools like directory systems, scripts, spreadsheets, etc. Consolidation of information gathered from those tools is a slow process that delays time-to-compliance and increases compliance costs. We recommend looking for consolidated, holistic tools that could replace those repetitive manual processes so that the scarce security talent could be shifted instead toward strategic tasks designed to improve compliance levels, allowing smaller teams to achieve better outcomes with less overhead. ESP is one of the most advanced tools on the market to achieve that goal, with its multitude of compliance, risk, and security controls management capabilities to automate many steps in the compliance management process.
Click here to request the ESP HITRUST white paper or an online demo
Related blog post: Compliance in the age of limited resources, the case for automation
